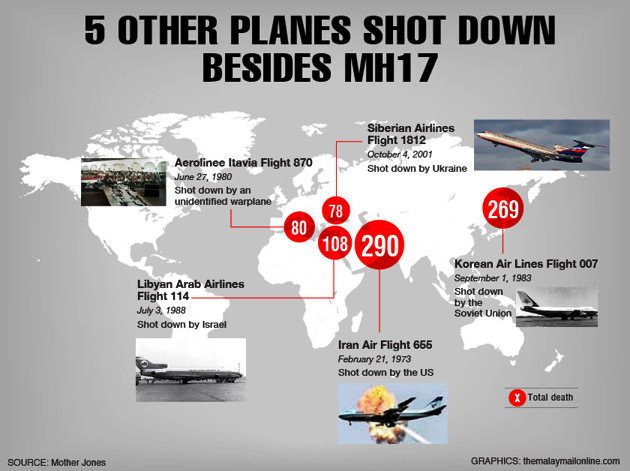
The concept of total security is fraught with problems. Perfect or absolute security is always the goal of security practitioners responsible for the protection of a facility or activity, but such a state of absolute security can never be fully obtained. The permutations to consider are in constant flux and calibrations and recalibrations are necessary. There is no asset so well protected that it can never be stolen, damaged, destroyed, or undermined by unauthorized individuals. For that reason a balanced, multilayered security program, informed and design after a thorough security vulnerability assessment provides protection against defined set of threats by informing the user of attempted intrusions and providing resistance to the would-be intruder’s attack paths. This resistance must be consistent around the intended asset protected perimeter area.
There are four main security elements that should be properly integrated in order to achieve a proper balance of physical security. They are:
- This is the process of detecting and locating intruders as far from the protected areas as feasible. Early detection gives the user more time for effective alarm assessment and execution of pre-planned response.
- Assessment is determining the cause of the alarm or recognizing the activity. This must be done as soon as possible after detection to prevent the intruder’s position from being lost.
- Intruders must be delayed long enough to prevent them from achieving their objectives before the response force can interdict them.
- A response force must be available, equipped, and trained to prevent the intruders from achieving their objective. The response time must be less than the delay time if the response force is to intercept the intruders before they achieve their objective.